- Generate Pre Shared Key Online Generator
- Generate Pre Shared Key Online
- Generate Pre Shared Key Online Login
- Generate Pre Shared Key Online Games
One of the more common issues identified during Wireless Network assessments is that organisations often utilise Pre-Shared-Keys (PSKs) for authentication, despite usually having relatively strong configurations for encryption.
WPA PSK (Raw Key) Generator The Wireshark WPA Pre-shared Key Generator provides an easy way to convert a WPA passphrase and SSID to the 256-bit pre-shared ('raw') key used for key derivation. The downside to creating a WiFi policy with a Pre-Shared Key is the hoops you have to jump through. So instead of using Apple Configurator or locating the WiFi XML File on a Windows device you can use these PSK XML Generators. Android WiFi PSK XML Generator 1.
- Your complete online vacation home organizer for family, friends and invited guests. Track dates with the group calendar, post house rules and instructions, enter your important contacts, make guests feel welcome with photos, maps and your own local guide, and more.
- The length of pre-shared key is from 8 to 63 characters. Finding a key with random 20 characters by the brute force method is impossible at a convenient time unless the passphrase is in the dictionary. For the purpose of demonstration, we are going to brute force a passphrase with 9 characters.
PSKs passphrase authentication ideally is only recommended for home networks, and for physically segregated corporate guest wireless networks. The risks associated with using PSKs are that by definition they are a shared secret, and thus can be statically known by one or more users. Key generator microsoft office 2010 free download. This can be partly mitigated by regularly changing the passphrases, but this itself would involve administrative input.
IPSec PSK Generator This tool allows you to generate pre-shared key (or PSK) for an IPSec tunnel with another party Pick a phrase, word, number sequence, whatever and use it as Key 1 on your side and have your partner do the same. For Key 2, have your partner pick something and put that in and communicate that to your partner.
- Create a WPA Key. This WPA Key Generator generate a WPA encryption key that you can use to secure your Wireless network. Generate the WPA Encryption key, copy it and paste it into your wireless router's configuration panel. Restart your DSL modem/router. Also check the WEP Key generator.
- WPA PSK (Raw Key) Generator The Wireshark WPA Pre-shared Key Generator provides an easy way to convert a WPA passphrase and SSID to the 256-bit pre-shared ('raw') key used for key derivation.
- Date (add/subtract) Date to Date (duration) Microsoft® Office 365® End Date Time Zone Converter Week Numbers Wifi Protected Access Pre-Shared Key. Barcode Generator Browser Headers Favicon Converter HTML to Markdown Converter Lorem Ipsum Generator OUI Lookup Password Generator Phonetic Alphabet Translator QR Code Generator.
All too often during wireless assessments do we see organisations using Pre-Shared-Key authentication for their main corporate wireless networks. More and more IT professionals are becoming security conscious as data breaches occur and securing wireless networks (and of course the connected devices) should be a priority due to the mobile nature of the modern office. Implementing a strong WPA2 802.1x configuration will greatly increase the security of those corporate wireless networks, although there are known weaknesses to be mindful of with certain configurations.
WLAN Key Generator Character Set 0-9, A-Z, a-z (ASCII 48-57, 65-90, 97-122) 0-9, A-Z, a-z + special characters (ASCII 33-126) 0-9. With Pre-Shared-Key authentication both the client (supplicant) and access point (authenticator, also known as ‘AP’) each attempt to prove that they know the PSK without actually disclosing this information. This process is called the 4-way handshake. Both the supplicant and authenticator each compute a Pairwise-Master-Key (PMK) from the.
So what are the security concerns?
With Pre-Shared-Key authentication both the client (supplicant) and access point (authenticator, also known as ‘AP’) each attempt to prove that they know the PSK without actually disclosing this information. This process is called the 4-way handshake. Both the supplicant and authenticator each compute a Pairwise-Master-Key (PMK) from the PSK passphrase and the AP’s SSID, which is then used as a basis for creating the rest of the key exchange data (further information below).
The weakness within this is that the majority of the information required to compute the plaintext PSK passphrase can be enumerated either through packet sniffing the access point (for example the SSID), or by capturing the traffic of the 4-way handshake itself. Essentially, the Message Integrity Code (MIC) is what is captured during the handshake and is what is used as a comparison during the cracking process to identify the plaintext PSK passphrase.
What is performed from an attacker’s perspective?
Sniper elite 3 license key generator. An attacker would initially need to identify a wireless network that uses PSK authentication. This can easily be performed by using the aircrack-ng suite of tools, specifically the airodump-ng tool. The first step of this process would be for an attacker to start a capable wireless card (or USB wireless adaptor) in monitor mode. This can be performed with the following command (as an example):
Once the device is in monitor mode, the main interface is taken down (as per the second command).
The next step in the process is to identify a target network. Using the airodump-ng tool and only specifying the monitor interface (in this example, mon0) allows the device to hop between wireless channels. This is not ideal for capturing a specific network handshake but is useful to locate the specific channel for the next step:
The results would show several networks, each with varying signal strengths and configurations, but in our example we will use channel 1 with the ‘SureCloud-WiFi’ AP.
Our next step is to target this network. We do that by specifying additional arguments for airodump-ng:
This command will capture wireless traffic to the file surecloud-wifi-capture-01.cap and will only focus on channel 1. Additional parameters can be specified, such as the use of –essid to target the network SSID name.
Once a handshake has been captured airodump-ng will note it at the top of the display. The next step following this is to clean up the capture file from any unnecessary packets not relating to the exchange, and to then ideally convert it to a hashcat-capable format for GPU processing. The following commands can be used to do this:
Using Hashcat is the most efficient way to perform password attacks such as dictionary attacks. How to use Hashcat is outside the scope of this article, but there are excellent resources available online:
- https://hashcat.net/wiki/doku.php?id=cracking_wpawpa2
- https://github.com/hashcat/hashcat
- https://www.blackmoreops.com/2014/03/27/cracking-wpa-wpa2-with-hashcat-kali-linux/
What is the background process behind this, from a technical point of view?
The key exchange handshake process uses several pieces of information, some of which is transferred over the air for the other device to make its necessary computations. This information includes:
- Pairwise Master Key (SSID, PSK)
- Authenticator Nonce (One-time key, generated by the Authenticator)
- Supplicant Nonce (One-time key, generated by the Supplicant)
- Authenticator MAC Address (Enumerated over the air)
- Supplicant MAC Address (Enumerated over the air)
Wpa2-psk Pre-shared Key Generator Manual
The Pairwise-Master-Key is never revealed over the air, but is used in a Pseudo-Random-Function alongside the key data (a concatenation of the Authenticator and Supplicant MAC addresses, and the Authenticator and Supplicant Nonces) to generate the Pairwise-Transient-Key.
As for the Pairwise-Transient-Key this is a 512 bit key, which is used to provide the following sub-keys:
- Key-Confirmation-Key (First 128 bits)
- Key-Encryption-Key (Second 128 Bits)
- Temporal-Key (Third 128 Bits)
- MIC Authenticator Tx Key (Fourth 64 bits) – Only used for TKIP
- MIC Authenticator Rx Key (Fifth 64 bits) – Only used for TKIP
The Key-Confirmation-Key (KCK) is the key that is used for the creation of the Message Integrity Code (MIC), which is what is ultimately used for computing the PSK passphrase by password cracking tools. The MIC key itself is calculated using a HMAC-MD5 algorithm.
Conclusion
From the perspective of an attacker that has captured the handshake, it is extremely difficult to compute the plaintext PSK passphrase, which is evidenced by the length of the process to compute just one MIC key for passphrase comparison. Common dictionary words (or slight variations of) should not be used for any wireless networks as these may be able to be computed within minutes. Regularly changing the passphrases is highly recommended, alongside using strong passphrases that use special characters and are not based on dictionary words – the longer the passphrase the better, up to the maximum 63 characters, but generally we would say a random strong passphrase should meet a 15 character minimum.
Wpa2 Psk Password
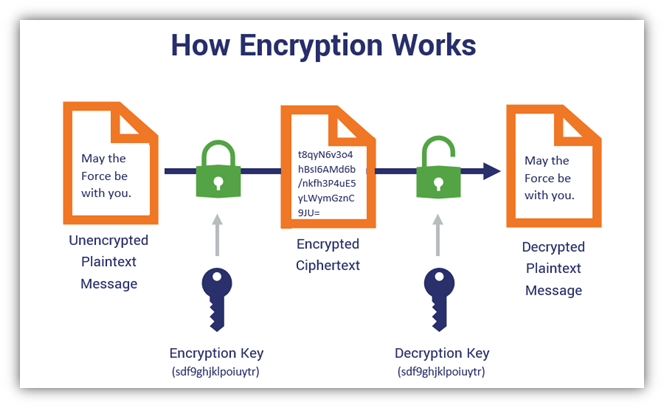
Furthermore, there are many resources online that can be used to obtain pre-computed SSID-PSK pairs for the most common wireless SSID names (such as ‘linksys’). These can be used to very quickly compute the actual passphrase used by a vulnerable network, and as such another recommendation is to not use common SSID names for networks as these would not appear in any pre-computed lists.
Wpa2 Psk Generator
References
Wpa2 Psk Vs Wpa Psk Wpa2 Psk
Find out more about our Cybersecurity services here.
This tutorial illustrates cracking of pre-shared key which is needed to gain an access to a WPA/WPA2 network. Instead of explaining the theory behind the attack, I focus on providing commands that you can easily copy and paste and penetrate the network. However, I strongly recommend getting a background to this topic by studying online resources before experimenting to understand what's going on under the hood.
Note: Tutorial is written for demonstration purpose only. I am not liable for any damage. Please, be aware that cracking into a network that is not your is illegal. Therefore, I highly recommend that you use your own devices.
Our goal is to to capture WPA/WPA2 authentication handshake and use aircrack-ng suite to crack pre-shared key. Handshake can be captured either in passive way, or active way. The passive way can be time consuming as an attacker waits for client to authenticate to WPA/WPA2 network. The active way speed up the whole process as an attacker deauthenticate an existing wireless client (all all clients) in order to obtain handshake. As a result, clients must re-authenticate. However, this method is loud and it may get unwilling attention, in case of many deauthentication attempts.
Passphrase:
The length of pre-shared key is from 8 to 63 characters. Finding a key with random 20 characters by the brute force method is impossible at a convenient time unless the passphrase is in the dictionary. For the purpose of demonstration, we are going to brute force a passphrase with 9 characters. The passphrase is in a notorious well known dictionary - rockyyout.txt.
WPA/WPA2 authentication handshake:
4-way handshake is the process of exchanging 4 messages between AP (authenticator) and client (supplicant) to generate encryption keys that are used to encrypt data sent over wireless medium. During handshake, PTK ( Pairwise Transit Keys) is generated and it is used to encrypt traffic between station and AP. PTK is unique between client and AP (1). Example of captured handshake between AP (94:44:52:4a:d1:54) and client (00:b5:d0:f0:c7:81) is depicted on the Picture 1.
Picture 1 - Example of 4-way Handshake
Note: Here is captured traffic with 4-way handshake file - output_file-01.7z.
Used Equipment:
AP: Belkin F5D8235-4 v2
AP MAC (BSSID): 94:44:52:4a:d1:54
ESSID: HackMeIfYouCan
Wireless AP channel: 1
Pasphrase: submarine
Client OS: Samsung Galaxy XCover 4
Client MAC : 00:b5:d0:f0:c7:81
Attacker OS: Linux Debian 10
Attacker MAC: 72:0d:2e:7d:2b:91
Wireless monitoring interface: wlp3s0mon
The wireless NIC and used kernel driver is depicted on the Picture 2.

Picture 2 - Wireless Network Card
1. Aircrack-ng Installation and Switching Wireless NIC from Managed to Monitor Mode
$ sudo apt install aircrack-ng
By default, wireless NIC is in managed mode and not associated with any AP (Picture 3).
Picture 3 - Wireless Network Card in Managed Mode
In order to capture all traffic on wireless channel without being associated with AP, we must switch wireless NIC from managed mode to monitored with the command:
$ sudo airmon-ng start wlp3s0
Once we enter the command, a new interface wlp3s0mon has been created (Picture 4).
Picture 4 - Wireless Interface wlp3s0mon in Monitor Mode
Note: In order to switch back from the Monitor to Managed mode, issue replace start with stop keyword.
2.1. Capture 4-way Authenitcation Handshake
Start capturing trafic on wireless channel on network with airdodump-ng utility. You may end up with an error message depicted on the Picture 5.
$ sudo airodump-ng wlp3s0mon
Picture 5 - RF-kill Error Message
In order to investigate the message, list the devices with the command:
$ sudo rfkill list all

Picture 6 - List of Blocked Wireless Devices
In order to unblock wifi device issue the command:
$ sudo rfkill unblock wifi
Generate Pre Shared Key Online Generator
Note: If your device is hard blocked, it may have be blocked by hardware switch (Fn + F9 combination for Lenovo) or in BIOS. Ii my case, hardware blocked device phy0 has been unblocked with the rfkill command, as well.
Picture 7 - Unblocked Wifi Devices
Check if we can run the airodump-ng command without any issues (Picture 8).
$ sudo airodump-ng wlp3s0mon
W have got MAC address of Access point of our interest - BSSID: 94:44:52:4A:D1:54. There is a station with MAC address 00:B5:D0:F0:C7:81 associated with the AP. If we are patient enough we should be able to capture handshake for any of BSSID listed in the Picture 8. As we have mentioned, this process depends entirely on how often clients autheticate to the WAP/WPA2 network.
Picture 8 - Getting 4-Way Authentication Handshake
Generate Pre Shared Key Online
Terminate the process of capturing 4-way handshake on the fly with CTRL-C key signal. We are going to capture traffic destined for AP with BSSID 94:44:52:4A:D1:54 and save it to the file output_file. Channel number is 1.
Generate Pre Shared Key Online Login
$ sudo airodump-ng --bssid 94:44:52:4A:D1:54 -c 1 --write output_file wlp3s0mon
Picture 9 - Getting 4-Way Authentication Handshake
Generate Pre Shared Key Online Games
2.2 Accelerate Process of Capturing 4-way Athentication Handshake
If they are not many wireless clients trying to authenticate to WPA/WPA2 network, the process of capturing 4-way handshake may take too long. In that case, aireplay may give us a hand and shorten the time required for the attack (Picture 10). This method, however, rely on de-authentication of existing wireless client from network which can have legal consequences.
$ sudo aireplay-ng -0 100 -a 94:44:52:4A:D1:54 wlp3s0mon
-0: deauthenticate all stations for particular AP
100: - number of dauthetications frames sent to all clients
-a MAC address of AP (BSSID)
Picture 10 - Sending Deauthetication Frames to ALL Stations Associated with BSSID 94:44:52:4A:D1:54
After while we have successfully captured 4-way handshake for BSSID 94:44:52:4A:D1:54 (Picture 11).
Picture 11 - Successfully Captured 4-way Handshake
Now, stop capturing traffic with Interrupt signal (CTRL-C).
3. Cracking Pre-shared Key
We are going to use aircrack-ng to crack the pre-shared key. In order to do this, we need to download a dictionary and hope that the key will be listed in the dictionary.
$ wget https://github.com/brannondorsey/naive-hashcat/releases/download/data/rockyou.txt
Once we get a dictionary rockyyou.txt, we can start the process of brute forcing passphrase (Picture 12). This can be quite intensive task for CPU as the aircrack-ng depends on entirely on CPU to find a key.
$ sudo aircrack-ng -w rockyou.txt -b 94:44:52:4A:D1:54 output_file-01.cap
Picture 12 - Pre-shared Key Found
After while, aircarck-ng found a pre-shared key submarine listed in the dictionary rockyou.txt. The average speed is 5346 keys per second when all CPUs are used (default option). To calculate your speed running aircarck-ng with the flag -S (Picture 13).
Picture 13 - Aircrack-ng Speed Test
To get info about your CPU, use aircrack-ng with the flag -u.
Picture 14 - Checking CPU Type with Aircrack-ng
End.