Hi all,Here is the link that you need for this tutorial: Intel SGX SDK download: the version. With the release of Intel SGX SDK v1.9, one important missing functionality of Intel SGX SDK is finally there: secure file I/O. It is provided in a component of Intel SGX SDK, named Intel Protected File System Library, which enables developers to perform I/O operations inside enclaves securely. More specifically, it guarantees. The Intel SGX SDK for Windows mentions that there is a simulation mode in page 65 'The simulation mode works in the same way as the debug mode except the fact that true hardware is not exercised, instead the Intel® SGX instructions are simulated in software.' The Intel SGX SDK is required to develop SGX enclaves and applications. It contains Intel custom libc and cryptographic libraries, each with 2 versions (debug & release). It also has tools such as sgxedger8r to generate glue code (we will discuss this in the enclave tutorial) and sgxsign to sign enclaves with development key.
Intel® Software Guard Extensions (Intel® SGX):
Intel® Software Guard Extensions (Intel® SGX) is an Intel technology for application developers who are seeking to protect select code and data from disclosure or modification. Intel SGX makes such protections possible through the use of enclaves, which are protected areas of execution. Application code can be put into an enclave by special instructions and software made available to developers via the Intel® SGX SDK. The Intel SGX SDK is a collection of APIs, libraries, documentation, sample source code, and tools that allows software developers to create and debug Intel SGX enabled applications in C/C++.
How do developers benefit from an SGX:
As platforms get hardened, attack surface moves to applications.
Application attacks typically do not cripple the entire application.
SGX offers developers fine grain, CPU-based security controls
CPU-based security is harder to compromise.
SGX Features:
- Intel® SGX Enhanced Application Code runs in Ring 3 only.
- Intel® SGX allows Applications to contain Enclaves.
- Enclaves protect code and data from disclosure or modification.
- SGX Enclaves are hardened by CPU-based security mechanisms.
- SGX Enclaves can also be remotely provisioned and attested.
Benefits of Intel SGX enclave:
- New Intel SGX instructions introduced with 6th Generation Intel® Core™ processor platforms.
- Relies on an Intel-provided driver and/or the OS for access to Intel SGX instructions and resource management.
- Executes within the context of its parent application, thereby benefiting from the full power of the Intel® processor.
- Reduces the trusted computing base of its parent application to the smallest possible footprint.
- Remains protected even when the BIOS, VMM, OS, and drivers are compromised, implying that an attacker with full execution control over the platform can be kept at bay.
- Benefits from memory protections that thwart memory bus snooping, memory tampering and “cold boot” attacks on images retained in RAM.
- Uses hardware-based mechanisms to respond to remote attestation challenges that validate its integrity.
- Can work in concert with other enclaves owned or trusted by the parent application.
- Can be developed using standard development tools, thereby reducing the learning curve impact on application developers.
Sub-Components of SGX:
- Platform
CPU Instructions
Firmware (for Platform Services)
BIOS - Software
SDK
Platform Software (re-distributable component) - Service
Provisioning (getting the SGX EPID key to the platform)
Attestation (Remote and Local Attestation (ensuring the enclave was correctly instantiated))
Download the SDK from following path:
https://software.intel.com/en-us/sgx-sdk
Software Requirements:
- Microsoft Windows* 7/ 8.1/10 64-bit version
- Microsoft Visual Studio* 2012 Professional/Ultimate Edition only
- Intel® Parallel Studio XE Professional Edition for Windows* Version 2013
Supported Languages:
Enclave binding interface supported in C/C++ only
What is Simulation Mode in SGX Enhanced Application:
The simulation mode works in the same way as the debug mode except the fact that true hardware is not exercised (Sky-Lake Platform), instead the Intel® SGX instructions are simulated in software.
One of the Project configurations to build an enclave in Microsoft Visual Studio* 2012.
Running in simulation mode does not require Intel® SGX hardware/driver. However, it does not provide hardware protection.
Note:
Custom exception handling is only supported in Hardware mode (Sky-Lake Platform).
Although the exception handlers can be registered in simulation mode, the exceptions cannot be caught and handled within the enclave.
How to Use Simulation Mode in SGX Enhanced Application:
Using the Simulation Libraries to run application enclaves in simulation mode (Intel® SGX hardware is not required).
What is Simulation Libraries:
The Intel® SGX Evaluation SDK provides simulation libraries to run application enclaves in simulation mode (Intel® SGX hardware is not required).
There are an untrusted simulation library and a trusted simulation library.
The untrusted simulation library provides the functionality that the untrusted runtime library requires to manage an enclave linked with the trusted simulation library, including the simulation of the Intel® SGX instructions executed outside the enclave: ECREATE, EADD, EEXTEND, EINIT, EREMOVE, and ECREATE.
The trusted simulation library is primarily responsible for simulating the Intel® SGX instructions that can executed inside an enclave: EEXIT, EGETKEY, and EREPORT.
'The simulation mode works in the same way as the debug mode except the fact that true hardware is not exercised, instead the Intel® SGX instructions are simulated in software.'
Create a Enclave and Application project using Microsoft Visual Studio* 2012 Professional/Ultimate Edition or Intel® Parallel Studio XE Professional Edition for Windows* Version 2013.
Follow the below steps to develop an SGX Enhanced Application
- Create Enclave Project
- Define Enclave Interface
- Import Enclave to Application
- Implement Application and Enclave Functions
- Compilation and Execution

Step 1: Create Enclave Project:
You can use Microsoft Visual Studio* Intel® Software Guard Extensions Wizard to create an enclave project. See Step by Step Enclave Creation for the detailed steps.
Is There An Sgx Sdk File
Step 2: Define Enclave Interface:
Use an EDL file to define the enclave interface, which exposes a trusted interface
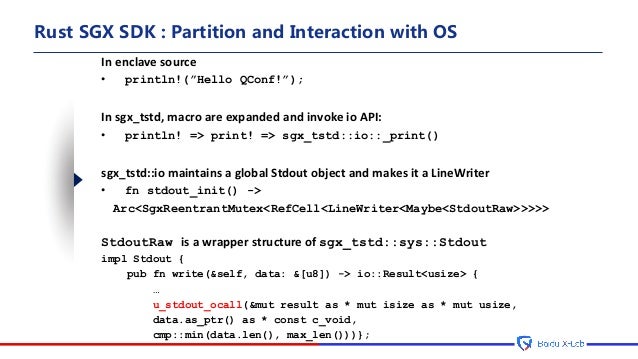
Step 3: Import Enclave to Application:
To call the enclave interface in the application, import the enclave to the application using Microsoft Visual Studio* Intel® Software Guard Extensions Add-in.
1. Right click the application project and select Intel® SGX Configuration -> Import Enclave. The Import Enclave dialog box opens.
2. Check the sample_enclave.edl box and press OK.
Step 4: Implement Application and Enclave Functions:
Implement the application and enclave functions
Step 5: Compilation and Execution
Now you can compile the application and enclave projects. After the compilation, set the working directory to the output directory and run the program.
Project Settings:
This section introduces the following project settings:
- Recommended Project Settings for an Enclave Project..
- Recommended Project Settings for an Untrusted Application.
To configure the project settings in Microsoft Visual Studio*, right click the project name in Solution Explorer and select Properties from the context menu.
1. Recommended Project Settings for an Enclave Project:
For an enclave, default project settings are recommended, with the following exceptions:
C/C++->General->Additional Include Directories:
$(SGXSDKInstallPath)include;$(SGXSDKInstallPath)includet-libc;$(SGXSDKInstallPath)includestlport;
Linker->General->Additional Library Directories:
$(SGXSDKInstallPath)bin$(Platform)$(Configuration)
Linker->Input->Additional Dependencies:
HW Configuration: sgx_trts.lib; sgx_tservice.lib; sgx_tstdc.lib; sgx_tstdcxx.lib; sgx_tcrypto_opt.lib - This is not use for Simulation mode. Used for DEBUG mode
Simulation Configuration: sgx_trts.lib_sim; sgx_tservice_sim.lib; sgx_tstdc.lib; sgx_tstdcxx.lib; sgx_tcrypto.lib
Linker->Input->Ignore All Default Libraries:Yes (/NODEFAULTLIB)
Linker->Advanced->No Entry Point:Yes
To sign the enclave during the build process, set a custom build step in the project settings:
Build Events->Post-Build Event->Command Line:
'$(SGXSDKInstallPath)binwin32releasesgx_sign.exe' sign -key '$(Pro-jectDir)sample_enclave_private.pem' -enclave '$(OutDir)sample_enclave.dll' -out '$(OutDir)sample_enclave.signed.dll' -config '$(ProjectDir)sample_enclave.config.xml' Note: The signing command line is a sample command. Change the command line based on the actual enclave name.
Build Events->Post-Build Event->Use In Build:Yes
2. Recommended Project Settings for an Untrusted Application:
Use the default project settings for an untrusted application, with the following additional settings:
C/C++->General->Additional Include Directories: $(SGXSDKInstallPath)include;
Linker->General->Additional Library Directories: $(SGXSDKInstallPath)bin$(Plat-form)$(Configuration)
Linker->Input->Additional Dependencies:
HW Configuration: sgx_uae_service.lib; sgx_urts.lib - This is not use for Simulation mode. Used for DEBUG mode
Simulation Configuration: sgx_uae_service_sim.lib; sgx_urts_sim.lib
Now we are able to run application enclaves in simulation mode (Intel® SGX hardware is not required) using Intel® SGX Evaluation SDK provides simulation libraries.
Please find the Sample code for SGX Enhanced Application using simulation mode at below link
GitHub* - https://github.com/surentharbe/Intel_SGX/tree/master/Simulation_Code
Confidential computing infrastructure requires specific tools and software. This page specifically discusses concepts related to application development for Azure confidential computing virtual machines running on Intel SGX. Before reading this page, read the introduction of Intel SGX virtual machines and enclaves.

To leverage the power of enclaves and isolated environments, you'll need to use tools that support confidential computing. There are various tools that support enclave application development. For example, you can use these open-source frameworks:
Overview
Is There An Sgx Sdk

An application built with enclaves is partitioned in two ways:
Is There An Sgx Sdk Download
- An 'untrusted' component (the host)
- A 'trusted' component (the enclave)
The host is where your enclave application is running on top of and is an untrusted environment. The enclave code deployed on the host can't be accessed by the host.
The enclave is where the application code and its cached data/memory runs. Secure computations should occur in the enclaves to ensure secrets and sensitive data, stay protected.
During application design, it's important to identify and determine what part of the application needs to run in the enclaves. The code that you choose to put into the trusted component is isolated from the rest of your application. Once the enclave is initialized and the code is loaded to memory, that code can't be read or changed from the untrusted components.
Open Enclave Software Development Kit (OE SDK)
Use a library or framework supported by your provider if you want to write code that runs in an enclave. The Open Enclave SDK (OE SDK) is an open-source SDK that allows abstraction over different confidential computing-enabled hardware.
The OE SDK is built to be a single abstraction layer over any hardware on any CSP. The OE SDK can be used on top of Azure confidential computing virtual machines to create and run applications on top of enclaves.
EGo Software Development Kit

EGo is an open-source SDK that enables you to run applications written in the Go programming language inside enclaves. EGo builds on top of the OE SDK and comes with an in-enclave Go library for attestation and sealing. Many existing Go applications run on EGo without modifications.
Confidential Consortium Framework (CCF)
The CCF is a distributed network of nodes, each running their own enclaves. The trusted node network allows you to run a distributed ledger. The ledger provides secure, reliable components for the protocol to use.
This open-source framework enables high throughout, fine-grained confidentiality, and consortium governance for blockchain. With each node using TEEs, you can ensure secure consensus and transaction processing.